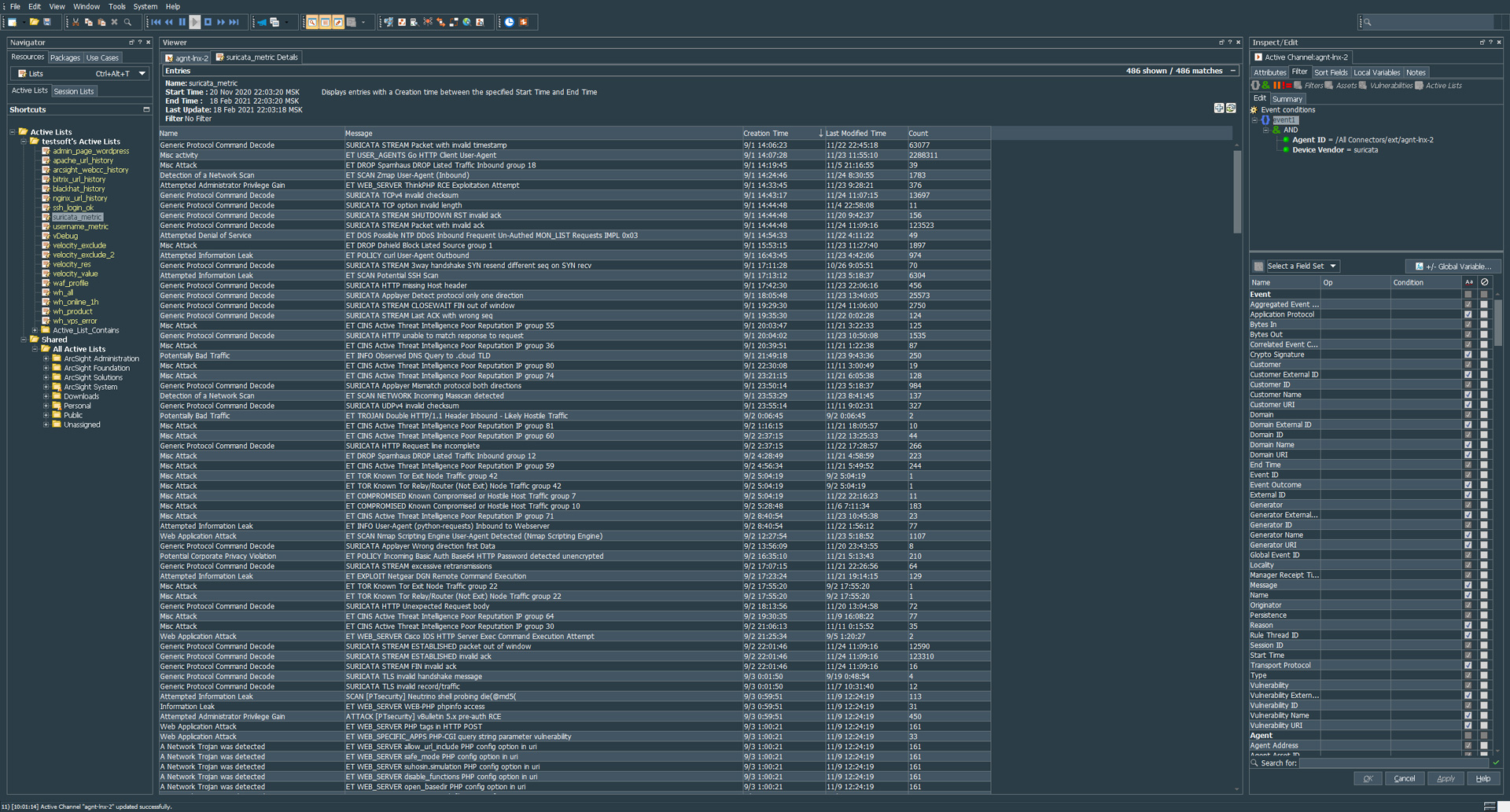
regex=(suricata)\\[.*\\]:\\s(.*) token.count=2 token[0].name=type token[0].type=String token[1].name=body token[1].type=String event.deviceVendor=__stringConstant(“suricata”) event.deviceProduct=__stringConstant(“ids”) event.sourceUserPrivileges=__stringConstant(“suricata”) event.deviceProcessName=__stringConstant(“suricata”) event.flexString2=body submessage.messageid.token=type submessage.token=body submessage.count=1 submessage[0].messageid=suricata submessage[0].pattern.count=1 submessage[0].pattern[0].regex=\\[\\d+:\\d+:\\d+\\]\\s+(.*)\\[Classification:\\s+([^]]+)\\].*}\\s+(\\d+.\\d+.\\d+.\\d+):\\d+\\s+\\-\\>\\s+(\\d+.\\d+.\\d+.\\d+)\\:(\\d+).* submessage[0].pattern[0].mappings=$1|$2|$3|$4|$5 submessage[0].pattern[0].fields=event.message,event.name,event.attackerAddress,event.targetAddress,event.targetPort
Author: testsoft
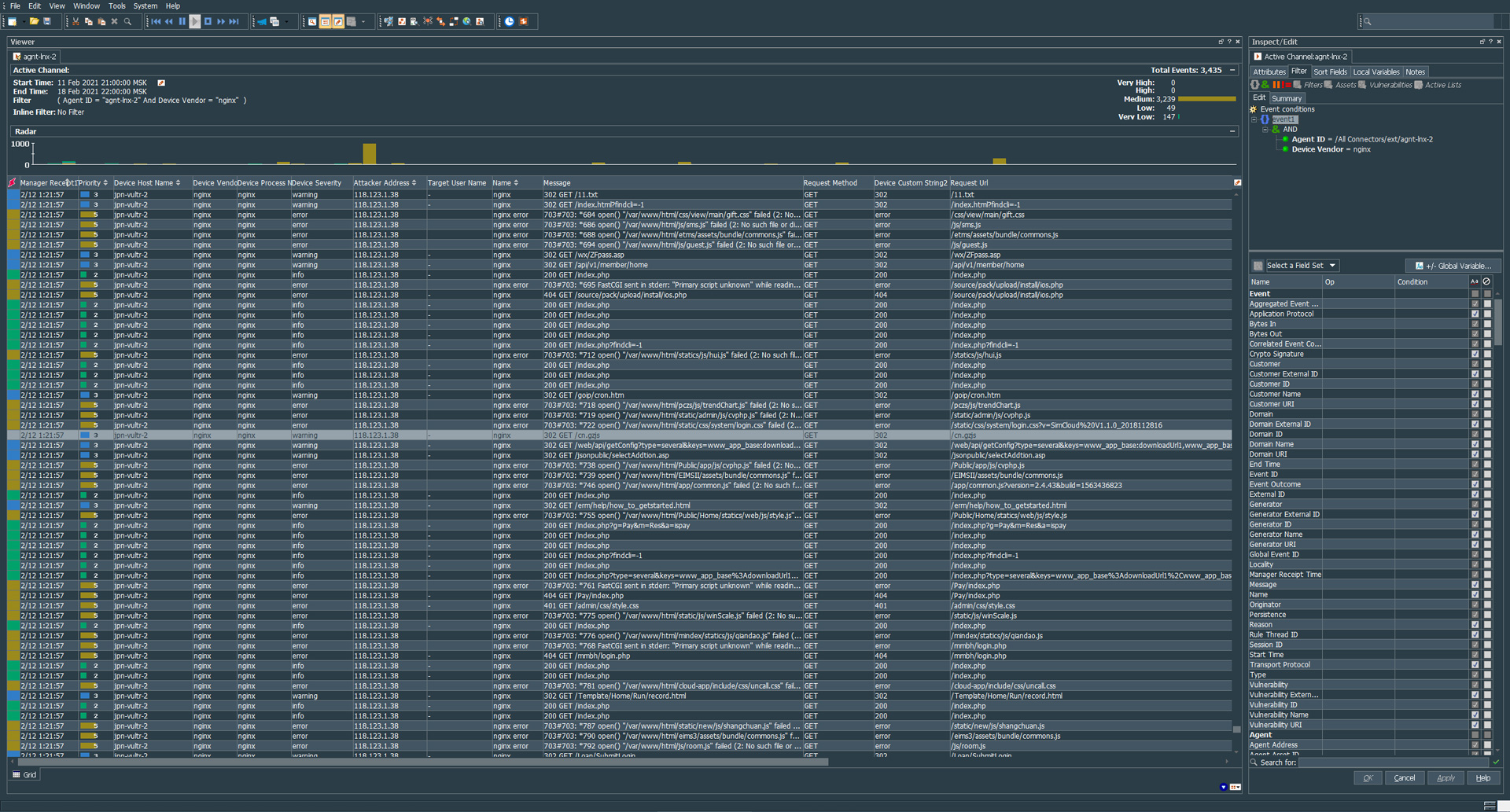
Arcsight flexConnector for Nginx with Bitrix
##################### # ### TESTSOFT.NET ### # ############################ ### ArcSight Parser For Nginx and Bitrix Stock Logformat v1.0 ### regex=(nginx):\\s(.*) token.count=2 token[0].name=type token[0].type=String token[1].name=body token[1].type=String event.deviceVendor=__stringConstant(“nginx”) event.deviceProduct=__stringConstant(“webserver”) event.sourceUserPrivileges=__stringConstant(“nginx”) event.deviceProcessName=__stringConstant(“nginx”) event.flexString2=body event.name=type event.message=body submessage.messageid.token=type submessage.token=body submessage.count=1 submessage[0].messageid=nginx submessage[0].pattern.count=5 #1.1.1.1 – – [29/Aug/2020:15:38:17 -0400] “GET /test/test/ HTTP/1.1” 401 597 “-” “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML,…
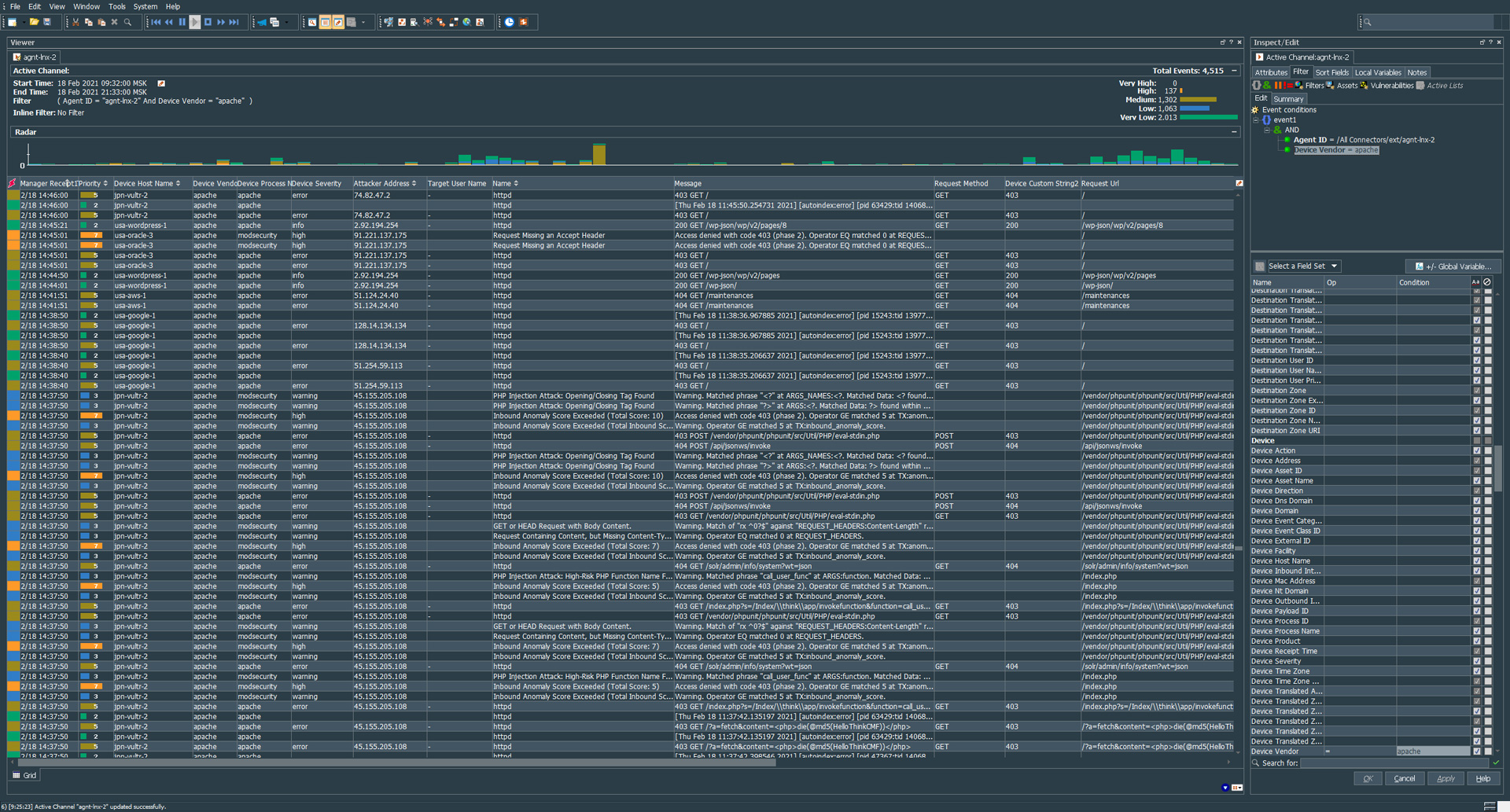
Arcsight flexConnector for Apache with modsecurity
The parser requires a little improvement, but in general, it processes 90% of incoming events. ##################### # ### TESTSOFT.NET ### # ############################ ### ArcSight Parser For Apache and ModSecurity Stock Logformat v1.0 ### regex=(httpd)(?:\\[.*\\])?:\\s(.*) token.count=2 token[0].name=type token[0].type=String token[1].name=body token[1].type=String event.deviceVendor=__stringConstant(“apache”) event.deviceProduct=__stringConstant(“webserver”) event.sourceUserPrivileges=__stringConstant(“apache”) event.deviceProcessName=__stringConstant(“apache”) event.flexString2=body event.flexString2Label=__stringConstant(“raw”) event.name=type event.message=body submessage.messageid.token=type submessage.token=body submessage.count=1 submessage[0].messageid=httpd submessage[0].pattern.count=3 ### Example ###…
Linux firewalld commands
Examples of simple commands when configuring firewalld sudo firewall-cmd –permanent –list-ports sudo firewall-cmd –permanent –list-service sudo firewall-cmd –permanent –list-all sudo firewall-cmd –get-active-zones sudo firewall-cmd –get-zone-of-interface=eth0 sudo firewall-cmd –permanent –zone=public –add-port=8080/tcp sudo firewall-cmd –permanent –zone=public –remove-port=8080/tcp sudo firewall-cmd –permanent –zone=public –add-service=http sudo firewall-cmd –permanent –zone=public –remove-service=http sudo firewall-cmd –permanent –zone=public –add-service=openvpn sudo firewall-cmd –permanent –zone=public –remove-service=openvpn…
Testsoft links
Parse Grokdebug Elastic.co/guide Syslog input plugin Winlogbeat quick start: installation and configuration Winlogbeat configure Windows System Monitor (Sysmon)
Install and setup filebeat for Elastic Cloud
To install filebeat, follow these steps
Installing kibana with nginx proxy. Centos 8.
Let’s consider one of the examples of installing the Kibana component, which is responsible for rendering in Elasticsearch.
Linux commands to view and find security events
Сollection of commands for auditing linux systems w who whoami last -f /var/log/btmp lastb /var/log/btmp — failed login attempts. /var/run/utmp — current login sessions /var/log/wtmp — list of all login sessions. id uname -a pwd ps -aux pstree ls -ltr ls -lah | tee content ls -la Which files are used by processes: lsof -i…